Mastering Temporary Email Service Identification for Robust Email Testing
Understanding Temporary Email Services
Did you know that nearly every online service today asks for an email address? (Do Scammers Have Your Email Address? Do This Now) While convenient, this often leads to spam and potential privacy risks. Temporary Email Addresses (TEAs) offer a solution, but understanding them is critical for robust email testing.
Temporary Email Addresses (TEAs) are disposable, short-lived email addresses. They allow users to sign up for services, trials, or other online interactions without exposing their primary email. Think of them as a shield against unwanted spam or a way to maintain privacy.
- TEAs are commonly used to avoid spam. Users can sign up for newsletters or promotions without the risk of their primary inbox getting flooded. (My email is being used to sign up for subscriptions and ...)
- They are also helpful for signing up for free trials. Some users extend trial periods by using multiple TEAs, as mentioned by Temp Mail. (Temp Mail - Disposable Temporary Email)
- Unlike regular email addresses, TEAs are designed to be temporary. Once their purpose is served, they can be discarded, protecting the user's identity.
TEA services operate by providing users with a temporary inbox. These services create, forward, and eventually expire these addresses.
- Many TEA providers offer features like custom domains. This allows users to create more legitimate-looking temporary addresses.
- API access is another common feature. This enables developers to integrate TEA functionality into their own applications.
- Examples of popular TEA providers include 10MinuteMail and Mailinator. These services offer easy-to-use interfaces for creating and managing temporary email addresses.
While TEAs offer benefits, they also pose risks in email testing. Their use can lead to inaccurate results and security vulnerabilities.
- TEA usage can skew testing results. For example, metrics like open rates and click-through rates may be artificially inflated.
- They can also increase spam and bot sign-ups. Malicious actors often use TEAs to create fake accounts, states Temp Mail.
- TEAs can be used to circumvent trial periods and promotional offers. This can lead to financial losses for businesses.
Understanding these risks is essential for developing effective strategies to identify and manage TEA usage. Next, we will explore methods for identifying temporary email addresses.
Methods for Identifying Temporary Email Addresses
Did you know that identifying temporary email addresses (TEAs) is like spotting a fake ID at a nightclub? It requires careful observation and the right tools. Here are some methods you can use to detect TEAs and protect your email testing environment.
One of the most straightforward methods is maintaining a list of known TEA domains. This involves compiling a database of domains used by services like 10MinuteMail and others. Regularly update this list to stay ahead of new and emerging TEA providers. You can also use regular expressions and pattern matching to identify domains that follow typical TEA naming conventions.
However, keep in mind that this method has limitations. New TEA domains pop up frequently, requiring continuous updates to your list. Without frequent updates, domain-based detection becomes less effective over time.
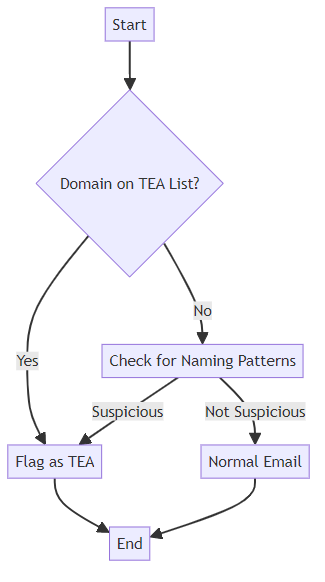
Heuristic analysis involves analyzing email address patterns and characteristics. Many TEAs use predictable naming conventions or formats. Look for suspicious email address formats, such as random strings of characters or unusually short addresses. Combining multiple checks, such as domain analysis and pattern recognition, can significantly improve accuracy. For instance, an email like "[email protected]" raises more red flags than "[email protected]."
Leveraging specialized email verification APIs offers a robust solution. These services provide real-time validation and comprehensive checks to identify TEAs. Integrating these APIs into your existing testing frameworks reduces maintenance overhead and improves accuracy. This is particularly useful in industries like finance, where security is paramount.
These services offer several benefits. They provide real-time validation, comprehensive checks, and reduce the burden of continuous updates. By using these services, you can streamline your testing workflows and ensure higher data quality.
Identifying TEAs is an ongoing process that requires a combination of methods. Next, we'll explore some advanced techniques for even more robust detection.
Implementing TEA Detection in Your Testing Workflow
Ready to put TEA detection into action? By integrating TEA detection into your testing workflow, you can prevent skewed results and safeguard your systems against abuse.
You can write code to validate email addresses against known TEA lists. This involves creating scripts that check the domain of an email address against a regularly updated list of TEA domains. You can also use regular expressions to identify patterns commonly found in TEA addresses, such as random character strings.
Automating the process of updating TEA domain lists is crucial. Consider a script that periodically fetches the latest list of TEA domains from a reliable source and updates your local database. Here's a simplified example in Python showing how you might check for TEA domains:
import re
def is_tea_domain(email, tea_domains):
domain = email.split('@')[1]
return domain in tea_domains
def is_suspicious_pattern(email):
pattern = r'^[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+.[a-zA-Z]{2,}$'
return not re.match(pattern, email)
email_address = "[email protected]"
tea_domains = ["10minutemail.com", "temp-mail.org"]
if is_tea_domain(email_address, tea_domains) or is_suspicious_pattern(email_address):
print("Potential TEA detected!")
else:
print("Email looks valid.")
Email verification APIs offer a more robust solution. They provide real-time validation and comprehensive checks to identify TEAs.
These APIs, like Mail7's email verification API, can be readily integrated to identify disposable email addresses and improve test accuracy. Mail7 offers features such as a disposable email testing API, a fast and reliable email delivery service, enterprise-grade security with encrypted communications, a developer-friendly REST API with comprehensive documentation, and unlimited test email reception.
Integrating with such APIs involves configuring API keys and handling API responses. You can then use the API to check if an email address is associated with a known TEA provider or exhibits characteristics of a temporary email.
When you identify a TEA, consider implementing soft bounces or warnings instead of hard bounces. Hard bounces can negatively impact your sender reputation. Clear messaging to users about TEA address restrictions also sets appropriate expectations.
You should also monitor TEA usage patterns and adapt your detection methods accordingly. This proactive approach ensures you stay ahead of emerging TEA services and techniques.
Implementing these practices into your workflow helps maintain data integrity and prevents abuse! Next, we will explore advanced techniques for temporary email detection.
Advanced Techniques for TEA Identification
TEA identification is constantly evolving, just like the methods used to create them. Let's dive into some advanced techniques to stay one step ahead.
One powerful approach involves training machine learning (ML) models to identify TEA addresses. These models analyze various features, such as domain age, email address structure, and usage patterns. By learning from large datasets of known TEAs, these models can accurately flag suspicious addresses.
ML can also incorporate natural language processing (NLP) to analyze email content and domain names, identifying linguistic patterns indicative of TEAs. For example, NLP can detect unusual word combinations or domain names that sound automatically generated.
- Improved accuracy in identifying TEAs.
- Adaptability to new TEA patterns as the model learns.
- Reduces reliance on static lists and rules.
However, this method requires substantial datasets and ongoing model training to maintain accuracy.
Another effective technique is leveraging community-maintained lists of TEA domains and patterns. These blacklists are compiled and shared by security professionals, researchers, and organizations, providing a broad range of TEA intelligence. Participating in collaborative filtering initiatives allows you to contribute and benefit from shared knowledge.
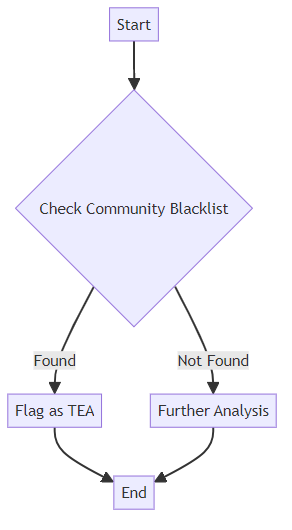
- Access to a wider range of TEA data.
- Reduced individual effort in maintaining TEA lists.
- Real-time updates from a community of experts.
The challenge lies in ensuring data quality and avoiding false positives, as community-driven data can sometimes be unreliable.
Monitoring user behavior patterns associated with TEA usage offers another layer of detection. This involves tracking activities such as rapid account creation, unusual login patterns, or suspicious transaction behavior.
Combining behavioral analysis with other TEA detection methods, like domain analysis and ML, enhances accuracy. For example, an account created with a known TEA domain that also exhibits rapid account creation behavior is highly suspicious.
- Identify suspicious activities that may indicate TEA usage.
- Combine behavioral data with other TEA detection methods for enhanced accuracy.
- Proactive detection of potential abuse.
However, ethical considerations and privacy implications must be carefully addressed when implementing behavioral analysis. Ensure compliance with data protection regulations and transparency with users.
Employing these advanced techniques can significantly enhance your ability to identify and manage TEAs effectively. Next up, we'll explore methods for email verification and validation.
Impact of TEA Detection on Email Deliverability and Reputation
Did you know that temporary email addresses (TEAs) can quietly erode your email marketing efforts? Detecting and managing these addresses is crucial for maintaining a healthy email ecosystem.
One of the primary benefits of TEA detection is reducing spam. By filtering out sign-ups from TEA providers, you minimize the amount of spam content entering your system. This leads to improved email deliverability rates. When you target legitimate users, your messages are more likely to reach their intended recipients.
Identifying and blocking TEAs also enhances your sender reputation. High bounce rates and spam complaints negatively impact your sender score. By reducing these issues, you maintain a positive reputation with email service providers.
TEA detection plays a vital role in preventing fraudulent activities. Malicious actors often use TEAs to create fake accounts for various nefarious purposes. Detecting these addresses helps mitigate risks associated with fake account creation and trial abuse.
By identifying and blocking TEAs, you safeguard sensitive data and intellectual property. This is particularly important in industries like finance, where security breaches can have severe consequences.
Detecting and managing TEAs helps maintain compliance with data privacy regulations like GDPR and CCPA. Ethical and transparent email marketing practices are essential for avoiding legal issues related to spam and unsolicited emails.
Adhering to these regulations builds trust with your audience and demonstrates a commitment to data protection. This proactive approach minimizes the risk of fines and legal repercussions.
As mentioned earlier, TEA services like 10MinuteMail offer temporary email addresses. Failing to detect and manage these can lead to skewed testing results and increased spam, as Temp Mail notes.
Effectively detecting TEAs protects your email deliverability, safeguards against fraud, and ensures compliance with regulations. Next, we will explore methods for email verification and validation.
Tools and Resources for TEA Identification
Ready to level up your TEA identification game? A variety of tools and resources exist to help you detect these temporary email addresses, each with its own strengths and weaknesses.
One approach involves using open-source TEA domain lists. These lists are community-maintained databases of domains known to be associated with temporary email services.
- Benefits: They offer free access, making them a cost-effective option for smaller organizations or individual developers.
- Limitations: You may need to perform manual updates and verification to ensure accuracy. The lists may not be comprehensive and could lag behind new TEA domain registrations.
For more robust and real-time detection, consider commercial email verification services. These providers offer a range of features designed to identify TEAs and other types of invalid or risky email addresses.
- Features: These services typically offer real-time validation, comprehensive checks, and API access for easy integration with your existing systems.
- Pricing: Commercial services usually have different pricing models and service level agreements (SLAs) to consider. Evaluate your specific needs and budget to choose the right provider.
Another option involves developing custom scripts for TEA identification. This approach gives you maximum flexibility and control over the detection process.
- Languages: You can use programming languages like Python and JavaScript to create scripts that check email domains against known TEA lists or use regular expressions to identify suspicious patterns.
- Benefits: You can tailor the scripts to your specific requirements and integrate them seamlessly into your existing workflows.
- Challenges: Requires technical expertise and ongoing maintenance to keep the scripts up-to-date and effective.
With the right tools and resources, you can significantly improve your ability to identify and manage TEAs. Next, we'll explore methods for email verification and validation.
Future Trends in Temporary Email Detection
The fight against temporary email addresses (TEAs) is far from over, and the future holds exciting advancements. What new techniques are on the horizon for identifying these elusive addresses?
Advancements in machine learning (ML) and artificial intelligence (AI) promise more sophisticated TEA identification. AI can analyze email content, domain names, and user behavior to detect patterns indicative of TEAs.
- AI algorithms can learn from vast datasets to identify subtle characteristics that humans might miss.
- For example, AI could detect unusual patterns in email registration data within healthcare platforms, flagging potentially fraudulent sign-ups.
- The potential for more accurate and adaptive TEA detection methods is substantial.
Blockchain technology offers a novel approach: decentralized TEA blacklists. This ensures improved transparency and security.
- A decentralized blacklist resists censorship, making it harder for TEA providers to circumvent detection.
- Imagine a retail environment where customer reviews are validated against a blockchain-backed list of known TEA users, preventing fake reviews.
- Challenges remain in terms of scalability and governance, but the potential is significant.
Combining TEA detection with identity verification services offers enhanced security. This involves verifying user identities using multiple factors.
- These factors include phone numbers, social media accounts, and biometric data.
- For instance, a financial institution might use identity verification to confirm a new user is not using a TEA before granting access to sensitive data.
- This integration has the potential to reduce fraud and abuse in online transactions.
In conclusion, AI-driven detection, decentralized blacklists, and identity verification integration represent promising future trends in TEA identification. As technology evolves, staying ahead in this cat-and-mouse game will require continuous innovation.





