Strengthening Email Security: A Deep Dive into Phishing Simulation and Training Platforms
Understanding the Phishing Threat Landscape
Phishing attacks are evolving at an alarming rate, making it harder than ever to spot a malicious email. Did you know that phishing was the most common type of cybercrime in 2020? Phish Insight notes that remote working has only exacerbated this issue.
Evolution of phishing techniques: Gone are the days of poorly written, generic emails. Today's phishing attacks are highly targeted, using spear-phishing techniques that leverage personal information to build trust.
- Spear-phishing examples: An attacker might send an email to an employee that looks like it's from their direct manager, referencing a recent project or internal meeting. The email could ask the employee to "urgently review a document" by clicking a link, which leads to a fake login page.
- Whaling examples: For high-profile targets like CEOs, attackers might craft emails impersonating a board member or a major client, requesting a wire transfer or sensitive company information. Subject lines could be as simple as "Urgent - Payment Required" or "Confidential - Action Needed."
The role of ai: Cybercriminals are now using ai to craft more convincing and personalized phishing campaigns. This includes generating realistic-sounding emails and creating fake login pages that are nearly indistinguishable from the real thing.
- Ai-generated lures: Ai can analyze publicly available information about an employee (like their LinkedIn profile) to create a phishing email that references their specific job role, recent activities, or even colleagues' names, making it incredibly believable.
- Deepfake voice/video: While not strictly email, ai is also used to create convincing voice or video messages that can accompany or precede phishing emails, further building trust.
Impact of remote work: The shift to remote work has increased phishing vulnerability. Employees working from home may be less vigilant and more likely to fall for scams.
- Home network risks: Employees might use less secure home networks, making them more susceptible to man-in-the-middle attacks that can intercept or alter emails.
- Reduced oversight: The lack of direct supervision in an office environment can mean employees are less likely to double-check suspicious requests with colleagues.
Business Email Compromise (BEC): BEC attacks involve impersonating executives or trusted vendors to trick employees into transferring funds or sharing sensitive information. These attacks can have a devastating financial impact.
- BEC email examples: An email might appear to be from the CFO asking an employee in accounts payable to "immediately process an urgent payment" to a new vendor, providing fake bank details. Or, it could be from a "vendor" requesting an updated W-9 form, which is actually a form designed to harvest sensitive company financial data.
Credential harvesting: Phishers create fake login pages that mimic legitimate websites to steal usernames and passwords. This is especially dangerous because employees often use the same credentials across multiple platforms.
- Credential harvesting email examples: An email might claim there's a "security alert" on your Microsoft 365 account and provide a link to "verify your login details." The link leads to a page that looks exactly like the Microsoft login page, but any credentials entered are sent directly to the attacker.
Malware distribution: Malicious attachments and links are common phishing tactics. Clicking on these can lead to the installation of malware, ransomware, or other harmful software.
- Malware attachment examples: An email might arrive with an attachment disguised as an invoice, a shipping notification, or a resume. When opened, the attachment executes malicious code, infecting the user's computer.
Social engineering tactics: Phishing emails often use social engineering tactics to manipulate victims. This includes creating a sense of urgency, exploiting authority, and building trust.
- Urgency examples: "Your account will be suspended in 24 hours unless you verify your information."
- Authority examples: "As per the CEO's directive, please forward this report immediately."
- Trust examples: An email from a "colleague" asking for help with a "quick task" that involves clicking a link or downloading a file.
Lack of awareness: Many employees lack the awareness and training needed to identify phishing attacks. This is a primary factor in why phishing remains so successful.
Cognitive biases: Cognitive biases, such as the tendency to trust authority figures, can make people more susceptible to phishing. Attackers exploit these biases to trick victims into taking harmful actions.
The cost of a single mistake: Just one employee falling for a phishing scam can have significant consequences, including data breaches, financial losses, and reputational damage.
Creating a 'security-first' culture: It's crucial to create a 'security-first' culture where employees are encouraged to report suspicious emails and prioritize cybersecurity best practices. Phriendly Phishing emphasizes that a culture of security involves short, relevant, and memorable training content developed by experts. Phish Insight provides data on the prevalence of phishing attacks, helping organizations understand the scale of the threat.
Understanding these aspects of the phishing threat landscape is crucial for developing effective defense strategies. In the next section, we'll explore how phishing simulation and training platforms can help organizations strengthen their email security.
What are Phishing Simulation and Training Platforms?
Did you know that a staggering 90% of successful cyberattacks start with a phishing email? (Statistics on Phishing Attacks - Huntress) That's why organizations are increasingly turning to phishing simulation and training platforms to strengthen their defenses. Let's explore what these platforms are and how they work.
Phishing simulation platforms are automated systems designed to mimic real-world phishing attacks. These platforms aren't about causing harm; instead, they're about helping organizations assess employee vulnerability and identify training needs. Think of it as a "friendly fire" exercise for your inbox.
Key features include:
- Customizable templates: Platforms offer a range of templates that can be tailored to mimic various phishing scenarios. This allows organizations to test their employees against different types of attacks.
- Realistic scenarios: The simulations often involve creating realistic-looking emails, complete with fake logos and urgent requests, to trick employees into clicking malicious links or providing sensitive information.
- Reporting capabilities: These platforms provide detailed reports on employee performance, highlighting areas where additional training is needed. This data-driven approach ensures that training efforts are focused and effective.
Security awareness training programs are educational initiatives designed to teach employees about phishing and other cyber threats. The goal is simple: change employee behavior and reduce susceptibility to attacks.
These programs come in a variety of formats, including:
- Videos: Short, engaging videos can be used to explain different types of phishing attacks and how to spot them.
- Quizzes: Interactive quizzes can help reinforce key concepts and test employee understanding.
- Interactive modules: These modules provide hands-on experience in identifying and responding to phishing emails.
- Live training sessions: In-person or virtual training sessions can provide a more personalized and interactive learning experience.
The true power comes from combining simulations and training. Simulations identify weaknesses, while training addresses them. It's a continuous cycle of assessment, education, and reinforcement.
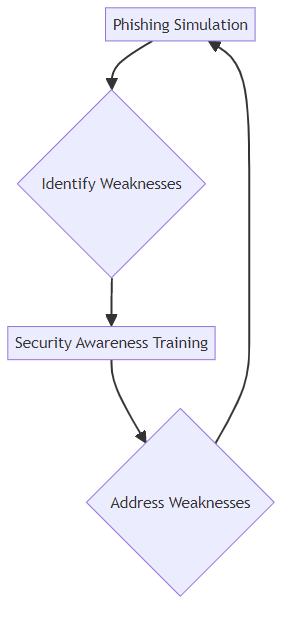
The simulations can be tailored based on the results of previous tests. For example, if a significant number of employees fall for a fake invoice scam, the training program can focus on teaching employees how to verify invoices and identify fraudulent requests. As Phriendly Phishing emphasizes, a culture of security involves relevant and memorable training.
By working together, phishing simulation and training platforms create a robust defense against phishing attacks, empowering employees to become a key line of defense.
Now that we know what these platforms are, let's dive into how to choose the right one for your organization.
Key Features and Functionalities of Effective Platforms
Is your organization truly ready to face a phishing attack? Effective phishing simulation and training platforms offer a range of features designed to transform employees from potential liabilities into a strong line of defense. Let's explore some key functionalities that make these platforms so valuable.
The effectiveness of a phishing simulation hinges on its realism. Platforms should offer diverse, real-world phishing examples. These templates must be customizable to mirror specific company contexts, such as mimicking internal communications or referencing familiar vendors.
- Real-world relevance: Simulations should reflect current phishing trends. For example, a healthcare provider might simulate an email claiming to be from a medical supply company requesting urgent password updates.
- Customization: A retail company could tailor templates to resemble customer service inquiries with malicious links, testing employees' vigilance in handling customer data.
- Multi-channel support: The best platforms support various phishing techniques, including email, SMS (smishing), and even voice (vishing) simulations. Consider a financial institution testing employees via SMS with fake fraud alerts.
Efficient campaign management is crucial for consistent training. Platforms should offer features like scheduling and automating phishing simulations, allowing administrators to set up campaigns in advance.
- Scheduling: IT departments can schedule simulations to run monthly or quarterly, ensuring continuous assessment.
- User segmentation: Platforms should allow for user segmentation and targeting, delivering tailored simulations to different departments or risk groups.
- Automatic enrollment: Automatic enrollment and management of trainees streamline the process, reducing administrative overhead. Phriendly Phishing offers automated phishing simulation and training that requires zero ongoing admin.
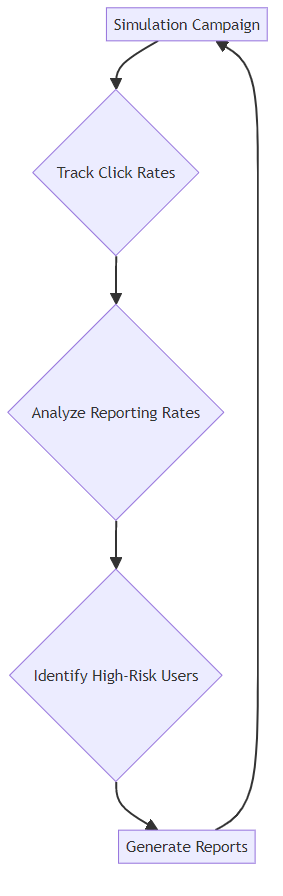
Actionable insights are essential for measuring the effectiveness of training. Platforms need to provide comprehensive reporting and analytics to track key metrics.
- Key metrics: Tracking click rates, reporting rates, and other key metrics helps identify areas for improvement.
- Risk identification: Identifying high-risk employees and departments allows for targeted interventions and additional training.
- Effectiveness measurement: Measuring the effectiveness of training programs over time demonstrates ROI and informs future strategies.
- Compliance: Generating reports for management and compliance purposes ensures accountability and transparency.
By focusing on these key features, organizations can leverage phishing simulation and training platforms to build a resilient human firewall.
Next, we’ll delve into how to integrate these platforms seamlessly into your existing security infrastructure.
Integrating Phishing Simulation with Email Testing and Development Workflows
Integrating phishing simulation into email testing and development might sound complex, but it's an impactful way to fortify your defenses. By incorporating these simulations into your existing workflows, you can proactively identify vulnerabilities and train your team to spot real threats.
One of the safest ways to test phishing simulations is by using disposable email addresses. Services like Mail7, Temp-Mail, or Guerrilla Mail allow you to create temporary email addresses for testing without risking real user accounts.
- Using disposable email addresses means that if a test email does happen to contain a live malicious link, it won't compromise your actual user data.
- For example, a financial institution could use disposable emails to test how employees react to a fake "urgent account update" request, without any real accounts at risk.
- With disposable email addresses, testing phishing simulations becomes a low-risk, high-reward activity.
Ensuring email delivery and avoiding spam filters are crucial for realistic simulations. Using SMTP testing tools helps guarantee your simulated phishing emails reach their intended recipients. Tools like Mailtrap.io, SendGrid's Sandbox mode, or Postmark's testing features are great for this.
- SMTP testing can prevent your simulations from being marked as spam, ensuring employees have the opportunity to identify and report the phishing attempt.
- Implementing email verification steps to validate email addresses before simulations ensures that your tests are sent to valid inboxes, improving the accuracy of your results.
- By avoiding blacklisting and maintaining a positive sender reputation, you can ensure that your phishing simulations are effective and realistic.
To streamline the process, consider leveraging Email APIs to automate the creation and delivery of phishing simulations. These APIs can integrate with your existing development and testing tools for a seamless workflow. Many email service providers (like SendGrid, Mailgun, or Amazon SES) offer robust apis for this.
- For instance, a retail company could use an Email API to automatically generate and send fake customer service inquiries with malicious links, testing employees' vigilance in handling customer data.
- APIs can also track simulation results and trigger automated training modules for employees who fall for the phishing attempt.
- Email api integration can significantly reduce the manual effort involved in running phishing simulations.
By integrating phishing simulations into your email testing and development workflows, you create a more resilient defense against real-world threats.
Choosing the Right Platform for Your Organization
Choosing the right phishing simulation platform can feel like navigating a minefield, but fear not! With the right criteria, you can select a platform that fits your organization like a glove.
Before diving into platform features, it's crucial to understand your organization's unique requirements.
- Start by identifying specific phishing threats relevant to your industry and company. A financial institution, for example, might focus on BEC (Business Email Compromise) attacks, while a healthcare provider might prioritize simulations related to patient data breaches.
- Next, evaluate your current security awareness level. Conduct an initial assessment to determine how well your employees can identify phishing attempts.
- Finally, define clear goals for your phishing simulation and training program. Are you aiming to reduce click rates, increase reporting rates, or improve overall security culture?
With a clear understanding of your needs, you can now evaluate platform features and pricing.
- Start by comparing features such as simulation templates, automation capabilities, and reporting options. Does the platform offer customizable templates that can be tailored to your specific needs? Does it automate campaign scheduling and user management?
- Then consider the total cost of ownership, including setup fees, training materials, and ongoing support. Some platforms may have hidden costs or require additional investments in training content.
- Finally, check for compliance certifications and security standards. Ensure that the platform adheres to relevant industry regulations and data privacy requirements.
Here are some reputable phishing simulation and training platform vendors to consider:
- KnowBe4: A comprehensive platform offering a vast library of training content, advanced simulation features, and strong reporting. Good for organizations of all sizes.
- Proofpoint Security Awareness Training: Integrates well with Proofpoint's email security solutions, offering targeted training based on real threats. Suitable for mid-to-large enterprises.
- Cofense: Focuses on empowering employees to report phishing, with robust simulation and response capabilities. Excellent for organizations prioritizing a strong reporting culture.
- Phriendly Phishing: Known for its user-friendly interface and automated approach, requiring minimal admin effort. A good option for smaller businesses or those seeking simplicity.
- SANS Institute: Offers in-depth security awareness training and simulations, often geared towards more technical audiences or those needing specialized training.
A phishing simulation platform doesn't exist in a vacuum. Seamless integration with your existing security tools is essential for a holistic security posture.
- Check for compatibility with SIEM (Security Information and Event Management), SOAR (Security Orchestration, Automation and Response), and other security platforms. Integration allows for streamlined data sharing and incident response.
- Api availability is another crucial factor for custom integrations. Open apis enable you to connect the platform with your internal systems and workflows.
- Assess the platform's ability to share threat intelligence and improve your overall security posture. Can it provide insights into emerging phishing trends and help you proactively address vulnerabilities?
Choosing the right platform requires careful consideration of your organization's needs, platform features, and integration capabilities.
Best Practices for Running Effective Phishing Simulations
Want to turn your employees into a human firewall? Running effective phishing simulations is key, but it's more than just sending out fake emails. It's about creating a comprehensive program that educates, empowers, and evolves.
Setting clear objectives is the first step. Are you trying to reduce click rates, increase reporting, or change overall behavior? For example, a healthcare organization might aim to improve awareness of HIPAA-related phishing attacks.
Creating realistic scenarios is crucial for engagement. Use templates that mirror real-world threats and customize them to reflect your company's context. Avoid generic emails that are easily identifiable.
Avoiding overly complex simulations ensures employees focus on key indicators. Keep the emails concise, the requests clear, and the consequences understandable. Overly complicated scenarios can lead to confusion and frustration.
Informing employees about the purpose sets the stage for a positive experience. Explain that the simulations are designed to improve security, not to trick or punish them.
Providing constructive feedback is crucial after each simulation. Highlight what employees did well and offer specific tips for improvement. Focus on positive reinforcement to encourage engagement.
Avoiding shaming or blaming employees who fall for simulations is essential for maintaining trust. Create a safe environment where mistakes are seen as learning opportunities.
Tracking key metrics provides valuable insights into the effectiveness of your program. Monitor click rates, reporting rates, and other relevant data to identify trends.
- Key metrics to track:
- Click Rate: Percentage of users who clicked on a malicious link or opened an attachment.
- Reporting Rate: Percentage of users who correctly identified and reported the simulated phishing email.
- Time to Report: How quickly users report suspicious emails after receiving them. A shorter time indicates better vigilance.
- False Positive Reporting Rate: Percentage of legitimate emails that users incorrectly flag as phishing. This can indicate over-cautiousness or a lack of understanding.
- Training Completion Rate: Percentage of employees who complete assigned training modules.
- Training Engagement: How actively employees interact with training materials (e.g., time spent, quiz scores).
- Key metrics to track:
Adjusting training content based on simulation results ensures that your program stays relevant. If employees struggle with a particular type of attack, focus your training on that specific threat.
- Examples of adjusting training content:
- If many employees click on fake invoice links, develop a specific module on "How to Spot a Fake Invoice" that includes visual examples, red flags, and verification steps.
- If spear-phishing attempts targeting specific departments are successful, create targeted training scenarios and modules for those departments, using examples relevant to their daily tasks.
- If reporting rates are low, create training on "Why Reporting Matters" and "How to Report Effectively," perhaps with a simple, one-click reporting button demonstration.
- Incorporate more interactive elements like short videos, scenario-based quizzes, or even micro-learning modules delivered daily or weekly.
- Examples of adjusting training content:
Continuously improving your security awareness program helps stay ahead of evolving threats. Regularly update your simulation scenarios and training materials to reflect the latest phishing tactics.
By following these best practices, organizations can transform their employees into a strong line of defense against phishing attacks.
The Future of Phishing Simulation and Training
The future of phishing simulation and training is dynamic, with ai and gamification leading the charge. How can organizations stay ahead of increasingly sophisticated cyber threats?
Ai can craft personalized and realistic simulations, mimicking the latest phishing techniques.
- Ai-driven personalization examples: An ai could analyze an employee's recent online activity (e.g., browsing for specific software or services) and then generate a phishing email that appears to be a legitimate offer or update related to that activity. It could also dynamically adjust the language and tone of an email based on the employee's role and communication style.
Machine learning algorithms can identify high-risk employees who may need extra training. This helps organizations focus their resources where they're needed most.
Ai can also automate the creation and delivery of training content, ensuring employees receive timely and relevant information.
Gamification increases engagement by turning training into a fun and competitive activity.
- Gamification mechanics examples:
- Leaderboards: Displaying top performers in reporting suspicious emails or completing training modules.
- Points and Badges: Awarding points for correct answers, successful reporting, or completing training, with badges for achieving certain milestones.
- Challenges: Setting up weekly or monthly challenges, like "Spot the Phish" quizzes or "Report a Fake Email" contests.
- Virtual Rewards: Offering small tangible rewards or recognition for top performers, like gift cards or company swag.
- Gamification mechanics examples:
Interactive scenarios mimic real-world phishing attacks, giving employees hands-on experience in identifying and responding to threats.
Offering rewards and recognition for completing training and reporting suspicious emails reinforces positive behavior.
Staying up-to-date with the latest phishing techniques is crucial as cyber threats evolve rapidly. A recent IBM Report 2024 highlights the increasing sophistication of phishing attacks. For instance, the report noted a significant rise in phishing attacks leveraging AI-generated content to bypass traditional security filters.
Continuously adapting your training program ensures that employees are prepared for the latest threats.
Fostering a culture of security awareness encourages employees to remain vigilant and report suspicious activity.
The key to a strong defense is continuous adaptation and employee empowerment. By embracing these future trends, organizations can build a human firewall that stands strong against evolving cyber threats.