Mastering SPF, DKIM, and DMARC Configuration Testing for Email Security
Is your email ending up in the spam folder? Implementing SPF, DKIM, and DMARC is crucial for securing your email and ensuring it reaches the inbox. Let's dive into the basics of these essential protocols.
Sender Policy Framework (SPF) is an email authentication method designed to prevent email spoofing. It allows domain owners to specify which mail servers are authorized to send emails on behalf of their domain. SPF works by verifying the sender's IP address against a list of authorized IP addresses in the domain's DNS record. The SPF record includes mechanisms like "a", "mx", "ip4", and "include" to define these rules. Modifiers, such as "-all", can enforce strict policies, while "all" indicates a soft fail. When a receiving server checks an incoming email, it looks up the sender's domain's SPF record and compares the sending IP address to the authorized list. A "-all" modifier means any email from an unauthorized IP should be rejected outright, while "all" suggests it should be treated with suspicion, possibly landing in spam.
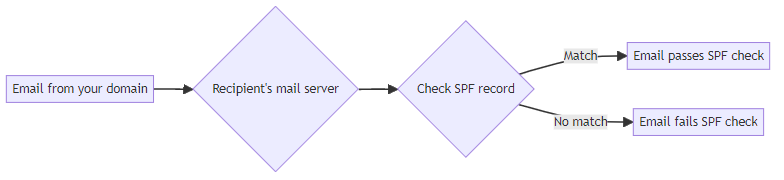
DomainKeys Identified Mail (DKIM) acts as a "digital notary" for your emails, verifying their authenticity and integrity. DKIM uses digital signatures to ensure that an email has not been modified during transit and comes from the right sender. DKIM uses a private key to add a digital signature to the email header. The recipient's server then uses a public key (published in the DNS record) to verify the signature. This process ensures both message integrity and sender authentication.
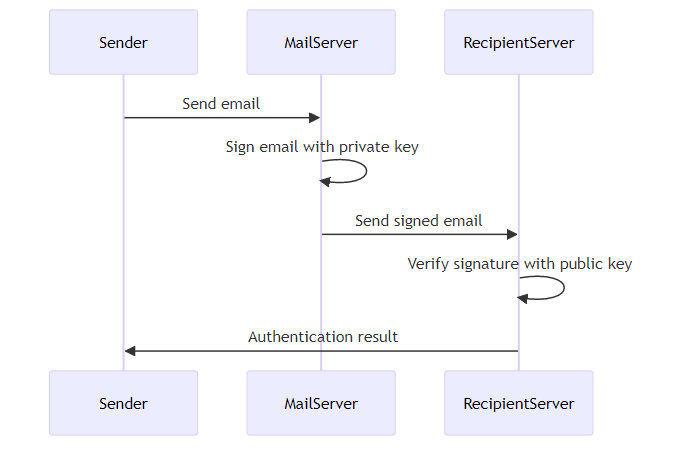
Domain-based Message Authentication, Reporting & Conformance (DMARC) builds upon SPF and DKIM to provide enhanced email security. DMARC allows senders to define policies for handling emails that fail SPF or DKIM checks. These policies can be "none", "quarantine", or "reject". A p=none policy means no action is taken, but reports are still sent. p=quarantine tells receiving servers to treat failing emails with suspicion, often sending them to spam. p=reject instructs servers to outright block emails that fail authentication. DMARC also provides a reporting mechanism, allowing senders to monitor email authentication results and identify potential issues. By unifying SPF and DKIM, DMARC offers a comprehensive shield against unauthorized use of a domain.
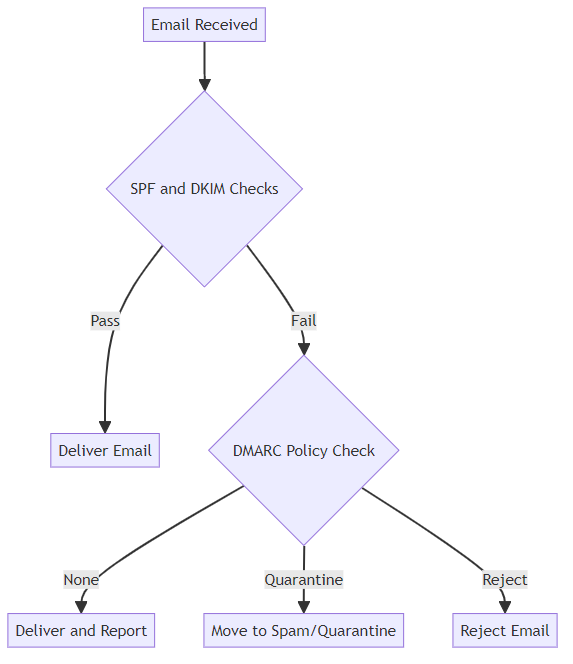
Implementing these protocols might seem complex, but it's essential for maintaining a strong email reputation. In the next section, we'll explore how to configure SPF records for email security.
Setting Up Your Testing Environment
Ready to put your email security to the test? Setting up a dedicated environment is key to validating your SPF, DKIM, and DMARC configurations without disrupting your live systems.
Selecting the right tools is crucial for effective testing. A variety of options are available, ranging from online SPF/DKIM/DMARC checkers to email analysis tools and command-line utilities.
- Online Checkers: Tools like MailReach SPF Checker, Smartlead tools, EasyDMARC tools, and URIports LearnDMARC provide quick and easy validation of your email authentication records. These are great for initial checks and troubleshooting.
- Command-Line Tools: For more in-depth analysis, command-line tools like
digandnslookupallow you to directly query DNS records. This can be particularly useful for verifying complex configurations.
Consider the accuracy, ease of use, and integration with your existing workflows when selecting your testing tools.
To avoid impacting your production systems, it's essential to use a dedicated test domain. Here's how to set it up:
- Dedicated Test Domain: Register a separate domain specifically for testing purposes. This ensures that any misconfigurations or issues won't affect your live email operations.
- Test Email Account: Set up a test email account with the appropriate SPF, DKIM, and DMARC records for your test domain. Verify that the DNS records are correctly configured to accurately simulate real-world scenarios.
- Temporary Email Services: Temporary email services can also be useful for testing purposes, allowing you to quickly create and dispose of email addresses as needed.
Creating realistic test scenarios is vital for comprehensive validation.
- Varied Sending Scenarios: Craft test emails that simulate various sending scenarios, including authorized servers, unauthorized servers, and forwarded emails.
- Diverse Email Clients and Methods: Use different email clients and sending methods to cover a wide range of potential issues. This ensures compatibility across various platforms and configurations.
- Content Types: Craft emails with different content types (plain text, HTML, attachments) to test DKIM signing and ensure proper handling of various message formats.
With your testing environment configured, you're ready to dive into configuring SPF records for email security.
Testing SPF Configuration
Is your SPF configuration a digital Fort Knox or a flimsy fence? Let's explore how to rigorously test your SPF setup to keep the bad guys out.
The first step is ensuring that all your legitimate email sources are correctly authorized.
- Use SPF testing tools like MailReach SPF Checker or Smartlead tools to check if authorized IP addresses and domains are correctly included in the SPF record.
- Send test emails from each authorized source (e.g., your CRM, marketing automation platform, and transactional email service) to confirm that SPF passes.
- Watch out for common SPF configuration errors, including syntax errors, exceeding DNS lookup limits, and incorrect IP addresses.
For example, a healthcare provider needs to ensure that their patient communication platform, appointment reminder system, and internal email servers are all authorized in their SPF record. Otherwise, legitimate emails might be flagged as spam.
The flip side of the coin is verifying that unauthorized sources are indeed blocked.
- Send test emails from unauthorized IP addresses and domains to confirm that SPF fails as expected.
- Analyze the results to ensure the receiving server correctly identifies the unauthorized source. Check email headers for SPF fail messages.
- Experiment with different "all" modifiers (
all, -all) to observe the impact on email handling. "-all" enforces a strict policy, meaning emails from unlisted sources should be rejected. "all" indicates a soft fail, where emails from unlisted sources are accepted but flagged as suspicious, often leading to them being sent to spam.
For instance, a retail company should test sending emails from personal email accounts or unapproved servers to ensure these messages fail SPF checks. This helps prevent attackers from spoofing their domain in phishing campaigns.
Even with careful configuration, SPF issues can arise. Here's how to tackle them:
- Be aware of common SPF issues and their solutions, including DNS propagation delays, incorrect syntax, and exceeding lookup limits.
- Use SPF record validators to identify syntax errors and other issues. Many online tools can help with this. Smartlead.ai offers a variety of free tools.
- Leverage DMARC reports to monitor SPF authentication results and identify potential problems. DMARC reports provide valuable insights into SPF failures and potential spoofing attempts.
Taking these steps ensures a robust SPF configuration that enhances your email security. Next, we'll delve into testing DKIM configurations for message integrity.
Testing DKIM Configuration
Is your DKIM setup truly fortifying your email security, or are there hidden vulnerabilities? Let's dive into DKIM configuration testing to ensure your messages are tamper-proof and authentically delivered.
The core of DKIM testing lies in confirming the presence and correctness of DKIM signatures.
- Begin by sending test emails to yourself or a dedicated testing service. Examine the email headers for the DKIM-Signature header. This header should be present and correctly formatted, containing essential information like the signing domain (
d=), selector (s=), and signature (b=). - Utilize online DKIM testing tools to validate the DKIM signature. These tools will verify the signature against the public key published in your DNS records, confirming the email's authenticity.
- Ensure that the domain used for signing (specified in the
d=tag) aligns with theRFC5322.Fromdomain (the address displayed to the user). This alignment is crucial for passing DMARC checks, as it confirms that the domain claiming to send the email is actually the one that signed it.
For example, a financial institution needs to guarantee that transaction confirmations are genuinely from them. A valid DKIM signature ensures customers can trust these emails, protecting against phishing attempts.
Comprehensive testing involves assessing DKIM's performance across diverse scenarios.
- Send test emails using various email clients (e.g., Gmail, Outlook, Thunderbird) to ensure DKIM signatures are consistently applied. Some email clients may handle signatures differently, so this step is crucial for broad compatibility.
- Test with different content types (plain text, HTML, attachments) to verify the DKIM signature covers the entire email. Attachments, in particular, can sometimes cause signing issues if not handled correctly.
- Verify that email forwarding does not break the DKIM signature. Forwarding can alter email headers, potentially invalidating the signature. Services that implement Sender Rewriting Scheme (SRS) can help mitigate this issue by rewriting the
Fromheader and adding a new DKIM signature to preserve authenticity through the forwarding chain.
For example, a marketing agency sending out newsletters must ensure DKIM signatures remain valid regardless of the recipient's email client. This maintains brand trust and ensures deliverability.
Even with careful setup, DKIM issues can arise. Knowing how to troubleshoot is vital.
- Be aware of common DKIM issues and their solutions: incorrect DNS configuration, key rotation problems, and signature validation failures. Verify that the DKIM key is correctly published in DNS using DKIM record validators.
- Analyze DMARC reports to monitor DKIM authentication results and identify potential issues. DMARC reports provide valuable insights into DKIM failures and potential spoofing attempts. As URIports.com notes, a DMARC monitoring service can provide detailed insight into your email channel.
Regularly rotating DKIM keys (at least every six months) is recommended to reduce the risk of compromised keys, according to URIports.com.
By thoroughly testing your DKIM configuration and promptly addressing any issues, you can significantly enhance your email security posture. Next, we’ll explore how to handle DMARC configurations to achieve robust email authentication and policy enforcement.
Testing DMARC Configuration
Don't let your emails get lost in the digital wilderness! Testing your DMARC setup ensures your email policies are enforced, protecting your domain from spoofing and phishing attacks.
The first step in testing your DMARC setup is to verify that your policies are actually being enforced. This involves:
- Sending test emails that fail both SPF and DKIM checks. Then, confirm that the DMARC policy is correctly applied. This means checking if emails are blocked, quarantined, or delivered based on your DMARC settings ("reject", "quarantine", or "none").
- Checking the recipient's spam folder or email logs. This confirms that emails failing authentication are handled according to the specified DMARC policy.
- Testing sub-domain policies (sp=none, sp=quarantine, sp=reject). To test this, you'd send an email from a sub-domain that should be covered by the policy. For example, if you set
sp=reject, send an email from an unauthorized sub-domain and verify it's rejected.
DMARC reports provide invaluable insights into your email authentication ecosystem. To leverage them effectively:
- Set up DMARC reporting (rua and ruf tags) to receive aggregate and forensic reports. The
ruatag specifies where to send aggregate reports (summaries of authentication results), whilerufdesignates the destination for forensic reports (detailed reports for individual failing emails). - Analyze DMARC reports to identify authentication failures, unauthorized sending sources, and potential security issues. These reports highlight where emails are failing authentication checks, helping you pinpoint misconfigurations or malicious activity.
- Consider using DMARC report analyzers to visualize and interpret the data in DMARC reports. These tools can help you quickly identify trends and anomalies.
- Automate DMARC report analysis to proactively identify and address email authentication problems. This ensures that you're always on top of your email security posture.
DMARC isn't a "set it and forget it" solution. It requires continuous refinement based on the data you gather.
- Use the insights from DMARC reports to refine SPF and DKIM configurations and address authentication failures. If reports show consistent SPF failures from a legitimate source, update your SPF record accordingly.
- Gradually transitioning from
p=nonetop=quarantineand then top=rejectas confidence in the configuration increases. Starting withp=noneallows you to monitor your email traffic without impacting delivery. - Regularly review and update DMARC policies to adapt to changing email infrastructure and security threats. Email environments are dynamic, so your DMARC policies should be, too.
As URIports.com points out, a DMARC monitoring service provides detailed insight into your email channel.
With your DMARC configuration tested and refined, you're well on your way to a secure email ecosystem. Next, we'll cover advanced testing techniques.
Advanced Testing Techniques
Want to take your email testing to the next level? It's time to explore advanced techniques that go beyond basic validation.
Here's how to leverage disposable email addresses, automated testing, and load testing to fortify your email infrastructure.
Disposable Email Addresses (DEA)
Disposable email addresses (DEA) are temporary, throwaway email accounts. Using them for testing helps assess email deliverability and spam filtering without cluttering your primary inbox.
- Leverage DEAs to test signup processes, verify email content rendering, and confirm that automated email workflows function correctly. For example, a QA tester for a social media platform can use DEAs to repeatedly sign up and trigger welcome emails, password resets, and notification settings.
- Create unique DEAs for each test to track email handling and identify potential issues. A software developer can use a new DEA for each iteration of an email template to ensure consistent rendering across different email clients.
- Automate DEA creation and management using apis and scripting. This allows for rapid, repeatable testing scenarios.
Automated Testing
Automated testing streamlines the validation process, ensuring consistent email security. By using apis and scripting, you can automate the sending and analysis of test emails.
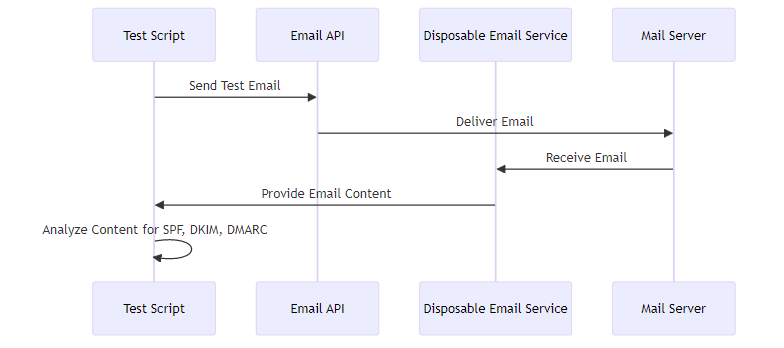
- Use email testing apis to automate the sending and analysis of test emails.
- Write scripts to generate test emails, send them to DEAs, and analyze the results. This includes checking for proper SPF, DKIM, and DMARC headers.
- Integrate automated email testing into CI/CD pipelines to ensure continuous email security. This ensures that every code change is validated for email deliverability and authentication.
Load Testing
Simulating high email volumes is crucial for assessing the performance and scalability of your email infrastructure. Load testing helps identify bottlenecks and optimize your setup to handle peak email traffic.
- Simulate high email volumes to assess the performance and scalability of email infrastructure. This is particularly important for e-commerce platforms during peak shopping seasons.
- Monitor email delivery rates, bounce rates, and spam complaints during load tests. This data helps identify potential issues with your sending reputation.
- Identify bottlenecks and optimize email infrastructure to handle peak email traffic. For example, a large marketing firm needs to ensure their email servers can handle sending millions of emails during a major campaign launch.
By incorporating these advanced testing techniques, you can proactively identify and address potential vulnerabilities in your email security setup.
Now that we've covered advanced testing, let's explore ongoing monitoring and maintenance strategies to ensure your email security remains robust.
Leveraging Mail7 for Comprehensive Email Testing
Is your email testing a tangled mess? It doesn't have to be! Mail7 offers a streamlined solution, simplifying the process and ensuring comprehensive validation.
Mail7 stands out as a leading solution, offering numerous benefits for developers needing robust email testing.
- Mail7 provides a Disposable Email Testing api, allowing for the creation of temporary email addresses for testing purposes. This ensures that your real inbox remains uncluttered and free from test data. You can use this api to send test emails to these disposable addresses and then retrieve the email content for analysis, directly verifying SPF, DKIM, and DMARC alignment.
- It features a fast and reliable email delivery service, guaranteeing that test emails are received promptly. Quick feedback is essential for efficient debugging and validation of your SPF, DKIM, and DMARC configurations.
- Mail7 incorporates enterprise-grade security with encrypted communications, ensuring that your test data remains private and protected. Security is a critical consideration, even in testing environments.
- The platform offers a developer-friendly REST api with comprehensive documentation, making integration into existing workflows seamless. Developers can easily incorporate Mail7 into their automated testing scripts to send emails and check their authentication status.
- Mail7 provides unlimited test email reception, allowing you to send as many test emails as needed without incurring additional costs. This is especially beneficial for load testing and extensive validation scenarios where you're sending numerous emails to test SPF, DKIM, and DMARC.
sequenceDiagram participant Tester participant TestScript participant Mail7API Tester->>TestScript: Run Test TestScript->>Mail7API: Create Disposable Email Mail7API->>TestScript: Return Email Address TestScript->>TestScript: Execute Email Test (Send email to disposable address) TestScript->>Mail7API: Retrieve Email (Check for SPF, DKIM, DMARC validity) Mail7API->>TestScript: Return Email Data TestScript->>Tester: Analyze Results
Mail7's focus on providing a comprehensive and developer-friendly environment makes it an ideal choice for email testing.
Harnessing the power of Mail7’s api, you can fully automate your email testing and achieve unprecedented efficiency.





