Securing Email Content: A Developer's Guide to Content Security Policy (CSP)
Understanding the Need for Email Content Security Policy
Here's a sobering thought: Email-based attacks are constantly evolving, making robust security measures more critical than ever. Are you prepared to defend your email content against sophisticated threats?
Common email-based attacks, such as cross-site scripting (XSS), clickjacking, and content injection, pose significant risks. These attacks exploit vulnerabilities in email clients and their rendering engines, potentially leading to data theft or malware distribution. Traditional email security measures like spam filters often fall short in preventing these sophisticated attacks.
These attacks can have devastating consequences across various sectors. For instance, in healthcare, a successful XSS attack could expose sensitive patient data. In retail, clickjacking might trick users into unknowingly making purchases or revealing financial information. Even in finance, content injection could be used to deliver phishing scams that steal credentials or install malware.
Content Security Policy (CSP) is a security standard designed to control the resources a web page can load. Adapted for email, CSP allows you to restrict the types of content that can be loaded and executed, significantly reducing the attack surface. According to UpGuard, CSP helps prevent cross-site scripting attacks (XSS), clickjacking, packet sniffing, and malicious content injection.
CSP offers several key benefits. It prevents the execution of malicious scripts, mitigates clickjacking attempts, and generally reduces the attack surface by limiting the sources from which content can be loaded. For example, CSP can prevent an email from loading external stylesheets or scripts from untrusted domains, blocking potential XSS attacks.
CSP should be viewed as part of a broader, defense-in-depth strategy. It complements existing security measures like input validation and output encoding, providing an additional safeguard against attacks. While CSP is not a replacement for these foundational security practices, it adds a crucial layer of protection.
Other essential email security measures include Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC). These technologies work together to authenticate email sources and ensure message integrity, further bolstering your email security posture.
Now that we understand the need for CSP, let's delve into how it works in practice.
Implementing CSP for Email: A Step-by-Step Guide
Are you ready to put theory into practice and implement Content Security Policy for your emails? Let's walk through the essential steps to safeguard your email content against potential threats.
First, you'll need to analyze the types of content used in your emails. Think about HTML, CSS, JavaScript, images, fonts, and other multimedia elements. This is crucial for determining what needs protection.
Next, identify the legitimate sources of these content types. This includes your domain, trusted Content Delivery Networks (CDNs), and any third-party services you rely on. For example, a marketing firm might use a CDN for hosting images included in their email campaigns.
Finally, create a detailed inventory of all allowed domains and subdomains. This inventory acts as your whitelist, ensuring that only trusted sources are permitted to load content.
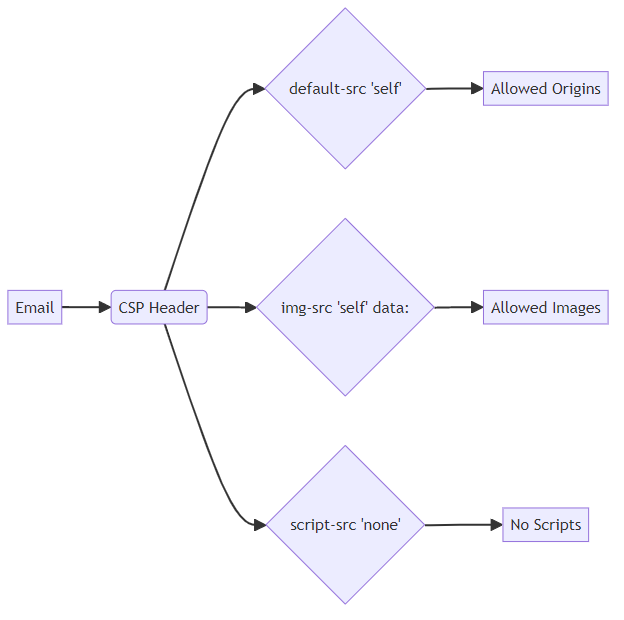
Now, let's get into the specifics of creating the CSP header. Construct the CSP header string by combining directives and their corresponding values. This string tells the email client which resources are allowed.
Key directives for email CSP include default-src, script-src, img-src, style-src, font-src, and connect-src. Each directive controls a specific type of resource. For example, img-src dictates from where images can be loaded.
Here's a sample CSP header tailored for a basic email content scenario:
Content-Security-Policy: default-src 'self'; img-src 'self' data:; script-src 'none'
In this example, only content from the email's origin ('self') and data URIs for images are allowed, while script execution is completely disabled.
With your CSP header crafted, it's time to deploy and test it. Inject the CSP header into your email sending process, typically through SMTP server configuration or an email API.
Use the Content-Security-Policy-Report-Only header for initial testing. This allows you to monitor policy violations without actually blocking content. Set up a report-uri or report-to endpoint to collect CSP violation reports.
Analyze these reports to identify any policy violations and adjust your CSP accordingly. This iterative process ensures your policy is effective without disrupting legitimate content.
As you refine your CSP implementation, remember that Microsoft Intune offers features like Enhanced Phishing Protection, which includes settings for automatic data collection and notifications for malicious activities, as detailed by Microsoft.
With your CSP implemented and tested, you're well on your way to securing your email content. Next, we'll explore advanced CSP techniques for even greater protection.
Essential CSP Directives for Email Security
Did you know that a single misconfigured CSP directive can leave your email vulnerable to devastating attacks? Let's examine critical CSP directives that act as the gatekeepers of your email content.
The default-src directive serves as the fallback for other, more specific directives. Think of it as the baseline policy for any resource type not explicitly covered by other directives. It dictates the permissible origins for various content types, ensuring that only trusted sources are allowed to load resources.
It's generally recommended to start with a restrictive default-src policy, such as default-src 'none', and then selectively enable specific content types with more granular directives. This approach minimizes the attack surface and provides a more secure foundation.
- Using
'self'allows content only from the email's origin, which is a good starting point. - Whitelisting specific domains, such as
default-src 'self' https://your-trusted-cdn.com, allows loading resources from your own domain and a trusted CDN.
script-src is arguably one of the most critical directives for preventing XSS attacks. It governs the origins from which JavaScript can be executed, providing a crucial defense against malicious scripts injected into your email.
The use of 'unsafe-inline' and 'unsafe-eval' is generally discouraged because they significantly increase the risk of XSS attacks. These keywords essentially bypass the protection offered by CSP, allowing inline scripts and dynamic code evaluation.
Instead, consider these alternative methods for allowing inline scripts:
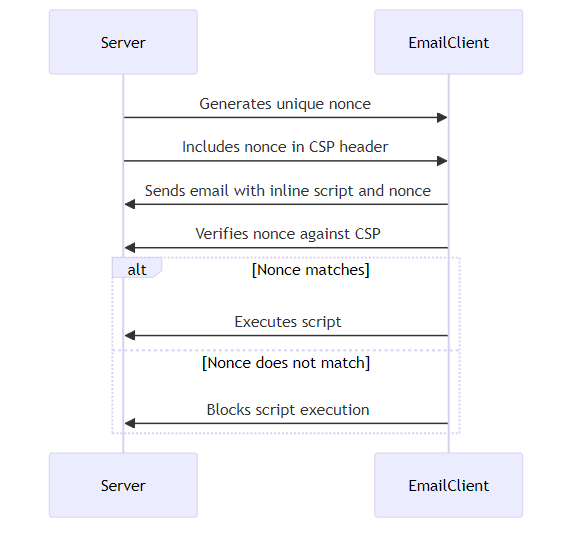
Nonces: A nonce is a cryptographic token that is generated dynamically by the server and included in both the CSP header and the
<script>tag.<script nonce="your-unique-nonce"> // Your inline script here </script>Content-Security-Policy: script-src 'nonce-your-unique-nonce'Hashes: A hash is a cryptographic digest of the script's content. The browser will only execute the script if its hash matches the one specified in the CSP header.
<script src="https://example.com/script.js" integrity="sha384-unique-hash"></script>Content-Security-Policy: script-src 'sha384-unique-hash'
These directives enable you to control the sources of specific resource types, providing fine-grained control over your email content.
img-src: Dictates the origins from which images can be loaded, preventing the display of malicious images or tracking pixels from untrusted sources. For example,img-src 'self' data: https://trusted-image-host.comwould allow images from the email's origin, data URIs, and a trusted image hosting service.style-src: Controls the sources of stylesheets, mitigating the risk of CSS-based attacks.font-src: Specifies the origins from which fonts can be loaded.connect-src: Restricts the URLs to which network requests (AJAX, WebSockets) can be made.
The data: scheme allows embedding images and fonts directly in the email, reducing external dependencies.
With these directives in your arsenal, you're well-equipped to construct a robust CSP for your emails. Now, let's delve into advanced techniques that can further enhance your email security posture.
Advanced CSP Techniques for Email
Did you know that allowing inline scripts is like leaving your front door unlocked? Let's explore how to keep your email secure with advanced Content Security Policy techniques.
Nonces and hashes offer a safer alternative to 'unsafe-inline' for allowing specific inline scripts and styles. Instead of broadly allowing all inline code, these methods enable you to whitelist only the code you trust.
- Nonces are cryptographic tokens generated dynamically by the server for each email. This means each email has a unique nonce, preventing reuse in potential attacks.
<script nonce="your-unique-nonce"> // Your inline script here </script>Content-Security-Policy: script-src 'nonce-your-unique-nonce' - Hashes are cryptographic digests of the script's content. The browser will only execute the script if its hash matches the one specified in the CSP header.
<script src="https://example.com/script.js" integrity="sha384-unique-hash"></script>
Nonces and hashes dramatically reduce the risk of XSS attacks by ensuring that only authorized inline scripts are executed.Content-Security-Policy: script-src 'sha384-unique-hash'
Implementing CSP is not a "set it and forget it" task. Continuous monitoring and refinement are crucial to ensure its effectiveness.
- Setting up a
report-uriorreport-toendpoint allows you to collect CSP violation reports. These reports provide valuable insights into which resources are being blocked and why. - Analyzing CSP reports helps identify policy violations and adjust the CSP accordingly. It allows you to fine-tune your policy to avoid blocking legitimate content while still maintaining a strong security posture.
- CSP reports can also help identify potential XSS attacks and other security issues. By monitoring the sources of blocked content, you can detect malicious activity and take steps to prevent it.
Integrating third-party content into emails, such as social media widgets or tracking pixels, can introduce security risks. It’s important to carefully evaluate third-party providers and their security practices.
- Use CSP to restrict the capabilities of third-party content as much as possible. For example, you can limit the domains from which third-party scripts can be loaded.
Content-Security-Policy: img-src 'self' https://www.example.com - As UpGuard warns, granular permissions will lower your attack surface, whereas broad permissions widen your vulnerable attack surface.
- Ensure that third-party providers adhere to security best practices and have a strong track record of protecting user data.
By implementing these advanced CSP techniques, you can significantly enhance the security of your email content and protect your users from sophisticated attacks. Next, we'll explore how to integrate CSP into your email workflow and automate testing.
CSP and Email Testing: Ensuring Compatibility and Security
Is your email's Content Security Policy actually working as intended across different email clients? Email testing is a critical step that ensures your CSP implementation doesn't inadvertently block legitimate content or create compatibility issues.
Thorough email testing is essential to ensure compatibility with various email clients and their rendering engines. CSP can significantly impact how emails are rendered and whether JavaScript code is executed. Therefore, you must test your CSP in a report-only mode before enforcing it. This approach allows you to identify potential issues without disrupting the user experience.
For example, a healthcare provider sending appointment reminders needs to ensure their CSP doesn't block critical images or links, leading to missed appointments and dissatisfied patients. Similarly, a financial institution sending account statements via email must verify that their CSP doesn't prevent users from accessing important account information.
Mail7 can be a valuable email testing solution for developers. It enables you to create disposable email addresses, access emails in real-time, and automate email testing workflows.
Mail7 offers a developer-friendly REST API and comprehensive documentation, making it easy to integrate into your existing testing processes. You can use Mail7 to test email rendering and CSP compatibility, ensuring your emails display correctly and that your CSP is functioning as expected.
To effectively test your emails with CSP:
- Test your emails with CSP enabled across various email clients like Gmail, Outlook, and Yahoo Mail.
- Analyze CSP violation reports to identify any compatibility issues and adjust your CSP accordingly.
- Automate email testing with Mail7 to ensure consistent and reliable results.
- Regularly review and update your CSP to address new threats.
By integrating CSP and rigorous email testing into your development workflow, you can create a secure and consistent email experience for your users. Next, we'll explore how to integrate CSP into your email workflow and automate testing.
Disposable Emails and Email Verification
Are you tired of your inbox overflowing with spam from test accounts? Disposable emails and email verification are your secret weapons for secure and efficient email testing.
Disposable emails, or temporary email addresses, are essential for developers during testing. These addresses let you:
- Avoid exposing your real email address, protecting it from potential spam or phishing attempts.
- Test registration processes, form submissions, and other email-dependent features without cluttering your primary inbox.
- Maintain a clean and organized testing environment, preventing accidental data leaks or security breaches.
Email verification is equally crucial to ensure you're sending sensitive information to valid recipients. This process involves:
- Validating the email address format to confirm it adheres to standard syntax rules.
- Confirming the existence of the domain to ensure the email server is active and capable of receiving messages.
- Reducing bounce rates, improving email deliverability, and maintaining a positive sender reputation.
As CSP and email testing help to ensure security, you could also consider Enhanced Phishing Protection. According to Microsoft, Enhanced Phishing Protection includes settings for automatic data collection and notifications for malicious activities.
By incorporating disposable emails and robust verification strategies into your workflow, you enhance the security and reliability of your email communications. Let's explore how to integrate CSP into your email workflow and automate testing.
The Future of Email Security and CSP
Is email security destined to become an AI-driven arms race? As email threats evolve, developers must leverage Content Security Policy (CSP) and explore innovative security strategies to stay ahead.
The threat landscape is constantly shifting, with attackers finding new ways to bypass existing security measures. Therefore, a static CSP is no longer sufficient; it must adapt to new attacks in real-time.
- Dynamic CSP generation could be a solution, where CSP policies are automatically adjusted based on the email's content. Imagine a system that analyzes the HTML, CSS, and JavaScript in an email and crafts a CSP on the fly, allowing only the necessary resources.
- Staying up-to-date with the latest CSP standards is also essential. As new directives and features are introduced, developers need to incorporate them to maximize protection.
- Regularly reviewing and refining CSP configurations is vital. A security policy from six months ago may not be effective against today's threats, making continuous adaptation a necessity.
Automation and Artificial Intelligence (AI) offer promising avenues for enhancing email security, automating tasks that once required manual intervention.
- AI can analyze email content to identify potential risks and generate CSP policies automatically. An AI-powered system could learn from past attacks and adapt CSP configurations to mitigate similar threats, enhancing protection in real-time.
- Automated testing is another critical area. By integrating CSP testing into the email workflow, developers can ensure that policies are effective and don't inadvertently block legitimate content. As mentioned earlier, Mail7 simplifies automated email testing, allowing developers to create disposable email addresses and access emails in real-time.
- Automation can also streamline the deployment of CSP. Instead of manually configuring each email server, developers can use automation tools to push out CSP policies across their entire infrastructure.
CSP is a powerful tool for securing email content, but it's only one piece of the puzzle. By embracing CSP and other security measures, developers can create a more secure email experience for their users.
- Developers must view CSP as a key component of their email security strategy. Continuous learning and adaptation are essential to stay ahead of evolving threats and keep email content safe.
- For developers seeking to delve deeper into CSP, resources like the Mozilla Developer Resources guide to the Content-Security-Policy offer comprehensive information and best practices.
- By prioritizing security and embracing innovation, we can create a future where email is a safe and reliable communication channel.
With an understanding of adaptive CSP and the role of AI, developers can confidently enhance their email security measures.