Email Spam Filter Evasion Techniques: A Developer's Guide
Email Spam Filter Evasion Techniques: A Developer's Guide
Understanding Email Spam Filters
Email spam: it's not just annoying, it's a serious security threat. Ever wonder how your inbox stays (relatively) clean? The answer lies in sophisticated spam filters that work tirelessly behind the scenes.
Spam filters are your email's first line of defense, analyzing incoming messages to identify and block unwanted content. They examine several factors:
- Content analysis: Filters scan for specific keywords or phrases commonly associated with spam, such as "free," "earn money," or explicit content.
- Header inspection: Filters check for inconsistencies or falsified information in email metadata, such as the sending domain or IP address.
- Sender reputation: Filters block emails from known spammer IP addresses or domains maintained in blocklists.
Effective spam filters use a multi-layered approach, combining different types of filtering techniques for comprehensive protection. Mimecast reports that their email spam filter SLA stops 99% of spam with a very low false positive rate. Real-time scanning is also crucial to keep up with the constant influx of email.
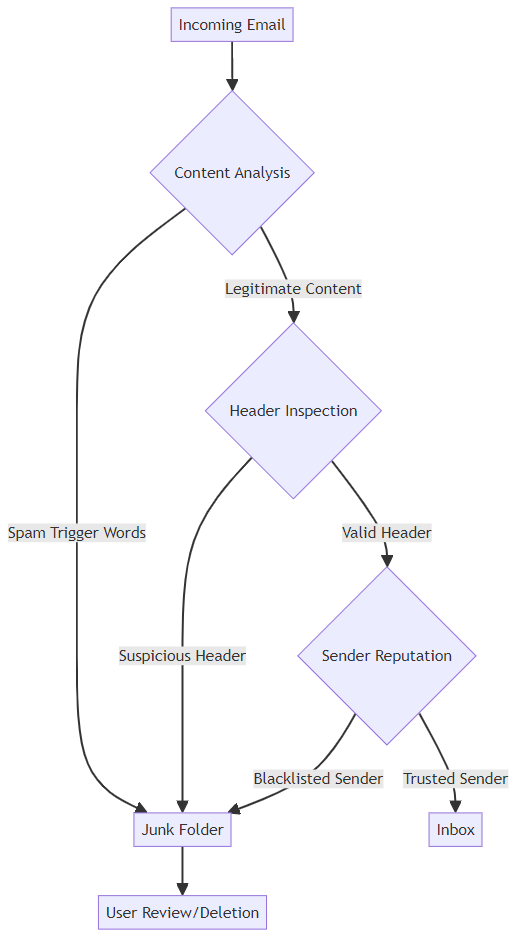
Several elements can trigger spam filters, landing your email in the junk folder.
- Spam trigger words: Avoid using words like "free," "earn," or "money" excessively, as these are common in spam emails.
- Excessive punctuation: Overusing exclamation points or question marks can also trigger filters.
- Broken HTML: Poorly formatted HTML can make your email look suspicious to spam filters.
- Unusual formatting: Things like excessive whitespace or text embedded in images can also be red flags.
Spam filtering has evolved significantly over the years. Early filters relied on simple keyword detection, but today's systems use advanced ai and machine learning. Bayesian filters, for example, learn from user-marked spam to identify new spam words. The shift from simple keyword-based filters to advanced ai-driven systems emphasizes the continuous adaptation required to counter evolving spam tactics. Machine learning algorithms now boast accuracy rates exceeding 97% across multiple phishing detection categories, including URL, email, and website-based attacks, according to a study. ((PDF) Machine learning based phishing detection from URLs)
Understanding how spam filters work is the first step in ensuring your emails reach their intended recipients. Next, we'll look at how spammers try to get around these filters.
Common Email Spam Evasion Techniques
Is your inbox constantly bombarded with unwanted messages? Spammers are always finding new ways to bypass filters, so let's explore some common techniques they use.
Spammers often manipulate email content to evade detection. This involves:
- Using synonyms and variations: Replacing common spam trigger words with similar terms. For instance, substituting "discount" for "offer" or "earn" for "make."
- Whitespace stuffing: Adding excessive spaces or invisible characters to alter the message's structure. This makes it harder for filters to identify typical spam patterns.
- Replacing text with images: Embedding text within images or using unconventional characters to bypass text-based analysis.
- Maintaining readability: Ensuring the email remains understandable while avoiding detection.
Forging email headers is another common tactic. This involves:
- Spoofing sender addresses: Making the email appear to originate from a legitimate source. This can trick recipients and bypass sender reputation checks.
- Routing information manipulation: Altering routing details to hide the true origin of the email.
- Ethical considerations: While understanding header manipulation is useful for defense, employing it can have serious legal and ethical implications.
- Countermeasures: Modern email systems employ various techniques to detect and prevent header spoofing. Understanding these countermeasures is crucial for developers to build defenses against malicious header manipulation.
Spammers frequently use multiple IP addresses and domain cloaking to avoid detection.
- IP rotation: Distributing email traffic across numerous IP addresses to prevent any single IP from being blacklisted.
- Domain cloaking: Hiding the actual destination of links using redirects or masking techniques.
- Compromised domains: Leveraging compromised or disposable domains to send spam.
- Detection methods: Techniques to identify and mitigate IP rotation and domain cloaking are crucial for robust spam filtering.
Understanding these techniques is vital for developers building and maintaining robust email security systems.
Ethical Considerations and Testing Boundaries
Navigating the world of email testing can feel like walking a tightrope – you want to test the limits, but you don't want to fall into unethical territory. So, how do you explore spam evasion techniques responsibly?
When you're testing email spam filters, it's easy to stray into ethically questionable areas.
- Understanding the line: It’s crucial to differentiate between legitimate testing and activities that could be considered malicious. For example, testing how filters react to various content types is fine, but sending unsolicited emails to a large number of recipients is not.
- Email marketing standards: Always comply with email marketing best practices, including the CAN-SPAM Act. This involves avoiding deceptive subject lines and providing a clear way for recipients to opt-out.
- Legal issues: Unauthorized email practices can have severe legal and ethical consequences, ranging from fines to damage to your company's reputation.
To test email deliverability safely, you need a controlled environment.
- Disposable email addresses: Use temporary email addresses and domains to avoid affecting real users. This ensures your tests don't inadvertently spam anyone.
- Simulation: Configure your testing environment to mimic real-world conditions without causing harm. This includes simulating different email clients and network configurations.
- Testing tools: Utilize specialized email testing tools and services to evaluate deliverability. These tools often provide insights into how your emails are likely to be treated by different spam filters.
Recipient consent is a cornerstone of ethical email practices.
- Explicit consent: Always obtain explicit consent from recipients before sending them emails. This demonstrates respect for their preferences and builds trust.
- Opt-in and opt-out: Implement clear opt-in and opt-out mechanisms. Make it easy for users to subscribe and unsubscribe from your emails.
- Avoid deception: Refrain from using deceptive practices like pre-checked boxes or misleading unsubscribe links. Transparency is key to maintaining a positive sender reputation.
By adhering to these ethical guidelines, you can conduct thorough email testing while respecting recipient privacy and maintaining legal compliance. Now, let's look at some tools and services you can use to safely test your emails without risking your sender reputation.
Leveraging Disposable Email Services for Testing
Are you tired of your inbox being flooded with test emails? Disposable email services provide a safe and efficient solution for QA, allowing you to rigorously test email functionality without compromising your primary accounts.
- Disposable email addresses are invaluable for signing up for services, submitting forms, and testing email workflows. This ensures your real email address remains protected from potential spam and security risks.
- By using temporary email addresses, you isolate test communications, preventing your main inbox from being cluttered with test data. This is particularly useful when testing new features or integrations that generate numerous emails.
- Disposable emails enable the automation of email verification and testing workflows. You can programmatically create and manage temporary inboxes, streamlining your testing process.
- These services ensure comprehensive test coverage without risking personal or business accounts. For example, you can simulate various user scenarios, such as multiple sign-ups or password resets, without affecting real users.
Mail7 offers a robust platform designed for email testing, providing developers with the tools they need to ensure reliable email functionality.
- Create disposable email addresses quickly and easily to use in testing environments. This helps keep your primary email accounts clean and secure.
- Access real-time emails to verify that your email systems are sending and receiving messages correctly.
- You can automate your email testing workflow, saving time and improving the efficiency of your testing processes.
Disposable email apis allow you to manage temporary email addresses programmatically, making email testing a seamless part of your development workflow.
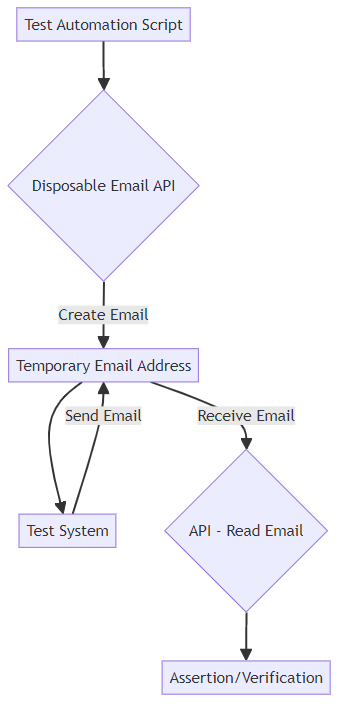
- Utilize disposable email apis to create and manage temporary email addresses programmatically. This enables you to generate unique email addresses for each test case, enhancing isolation and repeatability.
- Automate email testing processes through api integration to reduce manual effort and increase test coverage. This is particularly useful for continuous integration and continuous deployment (ci/cd) pipelines.
- Implement webhook notifications for real-time email reception, allowing your test scripts to react immediately to incoming messages.
- Here’s how you might create a temporary email address using the Mail7 api:
import requests
api_key = "YOUR_API_KEY"
url = "https://mail7.io/api/..." # Replace with actual Mail7 API endpoint
headers = {
"Authorization": f"Bearer {api_key}"
}
response = requests.post(url, headers=headers)
if response.status_code == 200:
print("Email address created:", response.json())
else:
print("Error creating email:", response.text)
With disposable email services and apis, you can streamline your email testing processes, ensuring your applications send and receive emails as expected.
SMTP Testing and Email Verification Techniques
Did you know that a single email can travel through multiple servers before reaching its destination? Ensuring your email infrastructure is robust and reliable requires thorough testing and verification, and that's where smtp testing and email verification techniques come in.
SMTP (Simple Mail Transfer Protocol) testing tools let you verify your email server's configuration. By simulating email transmissions, you can identify potential issues such as incorrect settings or connectivity problems. Regular smtp testing helps ensure your system can reliably send emails.
- Checking for open relays is crucial for security. An open relay allows anyone to send emails through your server, which spammers can exploit.
- You should also ensure proper authentication and encryption protocols are in place to protect sensitive information.
- Maintaining a secure email infrastructure prevents abuse and safeguards your sender reputation.
Email address verification apis help you validate email addresses. These tools check if an email address is properly formatted and active, reducing bounce rates and improving sender reputation.
- Implementing email verification prevents spam registrations and fake accounts on your platform.
- Verification apis enhance the quality and accuracy of your email lists, ensuring your messages reach real users.
- High-quality email lists lead to better engagement rates and more effective communication.
Understanding SMTP conversations is essential for troubleshooting email delivery issues. Analyzing smtp response codes helps you diagnose problems and ensure successful email transmission.
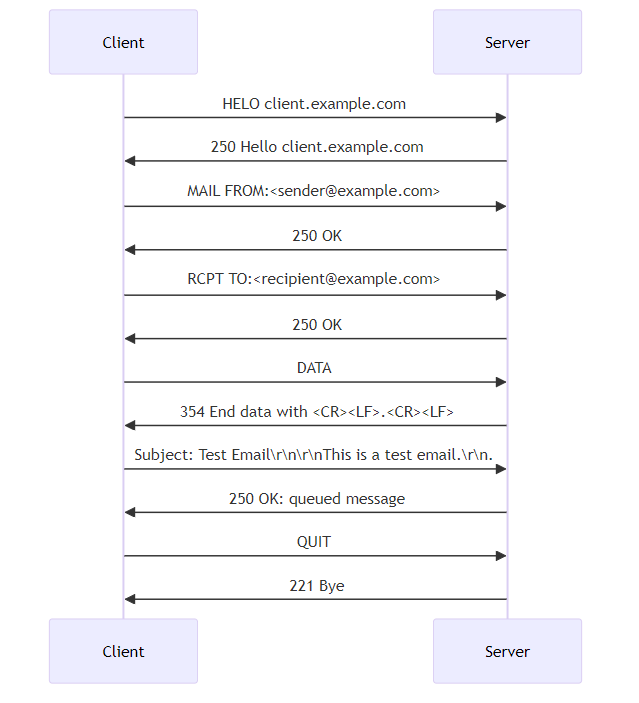
- A successful smtp transaction involves a series of commands and responses between the client and server.
- Analyzing failed transactions helps identify issues such as authentication failures or invalid recipient addresses.
- Understanding the role of smtp commands in email communication is crucial for effective troubleshooting.
By validating your email infrastructure and verifying email addresses, you can significantly improve your email deliverability and security.
Advanced Techniques for QA and Test Automation
Integrating automated testing into your email workflow can feel like adding a turbocharger to your qa process, greatly enhancing both speed and reliability. Let's dive into some advanced techniques that can revolutionize how you approach email testing.
Automated email testing is crucial for ensuring your emails render correctly and function as expected across different platforms and devices. Integrating email testing into your ci/cd pipelines allows for continuous validation, catching issues early in the development cycle. This integration ensures that every email update is automatically tested, reducing the risk of deploying faulty code.
- Selenium and Cypress are powerful tools for email ui testing. You can use these tools to simulate user interactions, such as clicking links and filling out forms, directly within the email client's interface.
- Email content verification and link validation can also be automated. Scripts can be written to check for broken links, verify that images load correctly, and confirm that dynamic content is displayed as intended.
- By automating these processes, you ensure consistent and reliable email functionality, reducing manual effort and improving overall quality.
To truly validate your email system, it’s essential to simulate how real users interact with your emails. Creating realistic email testing scenarios helps mimic user behavior, providing a more accurate assessment of your email’s performance.
- Simulating different email clients and devices ensures your emails render correctly across various platforms. This includes testing on desktop clients like Outlook, webmail interfaces like Gmail, and mobile devices with varying screen sizes.
- Email rendering can be tested across various platforms using services like Email on Acid or Litmus. These tools provide screenshots and reports, highlighting any display issues or compatibility problems.
- Addressing these compatibility issues proactively ensures a seamless user experience, regardless of the recipient's preferred email client.
Beyond functionality, it's crucial to assess how your email infrastructure handles high traffic volumes. Performance and load testing help identify bottlenecks and optimize email delivery.
- Conducting load tests assesses email server performance under high traffic, ensuring it can handle peak sending times without delays or failures.
- Identifying bottlenecks helps optimize email delivery, improving the speed and reliability of your email infrastructure. Monitoring email performance metrics and KPIs allows you to track key indicators such as delivery rates, open rates, and click-through rates.
- Ensuring the scalability and reliability of your email infrastructure is crucial for maintaining consistent service quality, especially during peak usage.
By integrating these advanced techniques into your qa and test automation processes, you can achieve a higher level of email quality and reliability.
Best Practices for Secure and Reliable Email Delivery
Email authentication and IP reputation are your email's gatekeepers; they significantly impact deliverability. Let's look at ways you can ensure secure and reliable email delivery.
- Email authentication protocols like spf, dkim, and dmarc verify email authenticity. These prevent spoofing and improve deliverability. Monitor dmarc reports to address authentication issues proactively.
- Maintaining a clean IP reputation avoids spam traps and blacklists. Use tools like Google Postmaster Tools to monitor, and implement list management best practices. This includes things like regularly cleaning your lists, never buying lists, and always honoring opt-out requests.
- Monitoring email delivery involves tracking open rates and click-through rates. Use feedback loops to remove invalid addresses and improve practices based on data. Feedback loops are basically a way for mailbox providers to tell you when an email has been marked as spam by a recipient. Setting them up helps you quickly identify and remove problematic addresses from your lists.
With these best practices, your emails will reach their intended destination.





