Email Authentication Protocols: A Developer's Guide to Secure Email Testing and Delivery
Email Authentication Protocols: A Developer's Guide to Secure Email Testing and Delivery
Understanding Email Authentication: Why Developers Should Care
Did you know that email spoofing can trick even savvy internet users? It's a serious threat, and that's why understanding email authentication is crucial for developers.
Email spoofing involves forging the sender's address to appear as a trusted source. This can damage brand reputation and lead to data breaches. For example, Amazon has an email address specifically for reporting potential scams, highlighting the prevalence of Amazon spoofing.
Phishing attacks are also becoming more sophisticated, making robust defenses essential. Cybercriminals spare no one and no opportunity.
Email authentication acts as a key defense against spoofing and phishing. It verifies the sender's identity and domain ownership, ensuring trust and improving deliverability.
Starting in 2024, major email providers like Gmail and Yahoo require email authentication for bulk senders. (Email Authentication Protocols in 2024: SPF, DKIM, DMARC & BIMI) As Email on Acid reports, these new requirements emphasize the importance of protocols like SPF, DKIM, and DMARC. Generally, a "bulk sender" is considered anyone sending a significant volume of emails, often exceeding a few thousand per day, though specific thresholds can vary by provider.
Developers play a vital role in implementing and maintaining email authentication. Integrating authentication into email testing and development processes helps build secure email applications.
Email authentication helps establish IP address and domain reputation, further enhancing security. Understanding these protocols is essential for building robust email workflows.
By implementing email authentication, developers contribute to a safer and more trustworthy email ecosystem. Next, we'll dive into the specifics of SPF, DKIM, and DMARC.
SPF: Authorizing Sending Sources
Is your domain being used by spammers without your knowledge? SPF can help prevent this. SPF is a crucial email authentication method that verifies the sender's IP address. (What Is SPF in Cyber Security? Understanding Sender ... - Darktrace)
SPF, or Sender Policy Framework, is a DNS TXT record that allows receiving mail servers to verify that an email claiming to come from a specific domain is associated with an authorized IP address. The receiving server checks the SPF record to ensure the email originates from an approved source. Without SPF, emails are more likely to be marked as spam.
Here's how it works:
- The domain owner creates an SPF record, listing authorized IP addresses.
- The record is published in the domain's DNS settings.
- When an email is sent, the receiving server checks the SPF record.
- If the sending IP matches an authorized IP, the email passes the SPF check.
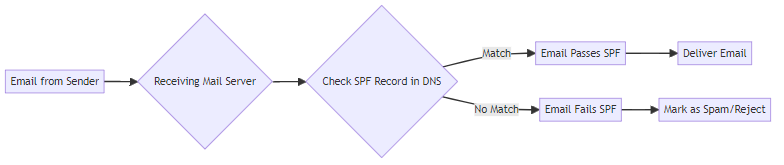
For example, an SPF record might look like this: v=spf1 ip4:192.0.2.0/24 include:_spf.example.com -all. This record authorizes IP addresses in the 192.0.2.0/24 range and includes any IP addresses authorized by _spf.example.com. The -all mechanism at the end specifies that any IP addresses not explicitly authorized should be rejected.
When creating SPF records, consider different email sending scenarios. For instance, if you use a third-party marketing automation platform, you need to include their IP addresses or domain in your SPF record. Common configuration errors, such as exceeding the DNS lookup limit, can cause SPF to fail. The DNS lookup limit is a restriction on how many DNS lookups an SPF record can perform (typically 10). Exceeding this limit means the SPF check can't be completed, leading to a failure.
It's also important to note a key limitation: SPF won't work when emails are forwarded. As Email on Acid explains, this is because the forwarded email's origin no longer matches the original SPF record.
Test your SPF records using online tools to verify their effectiveness. Check SPF authentication results to identify potential issues. If you're on a shared IP address, remember to update your SPF record when switching email service providers (ESPs).
Properly configured SPF records enhance email deliverability and protect against spoofing. Understanding SPF is crucial for building secure email workflows.
Next, we'll explore DKIM and its role in email authentication.
DKIM: Digitally Signing Emails for Integrity
Did you know that digitally signing your emails can significantly reduce the risk of tampering? DKIM is a powerful tool for ensuring email integrity.
DomainKeys Identified Mail (DKIM) adds a digital signature to the email header, verifying the sender and associating the message with a specific domain. This signature acts like a unique identifier, ensuring the email hasn't been altered during transit. Unlike SPF, DKIM signatures remain valid even when an email is forwarded.
DKIM relies on public and private keys. The sender's mail server uses a private key to create the digital signature, while the recipient's server uses the corresponding public key to verify it. The public key is stored in the domain's DNS record.
Here's a simplified view of the DKIM process:
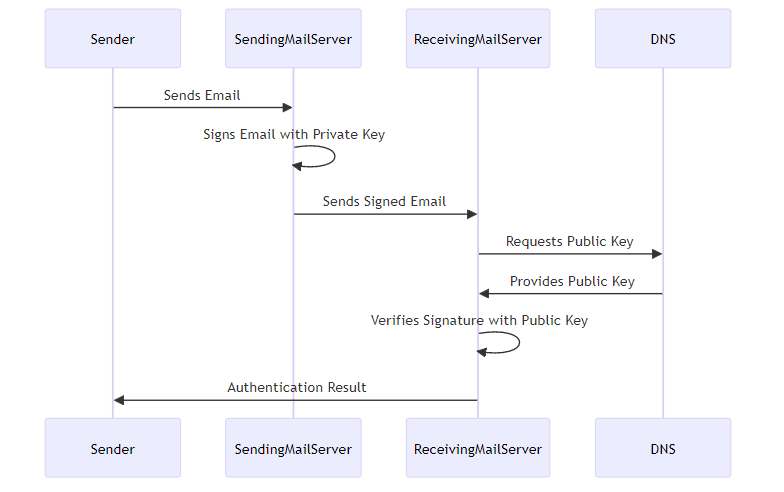
Generating DKIM keys and configuring DNS records involves several steps:
- Generate a private key and a corresponding public key.
- Publish the public key in your domain's DNS record as a TXT record.
- Configure your email sending application to use the private key to sign outgoing emails.
It's crucial to rotate DKIM keys a few times per year to maintain security. For example, organizations can schedule quarterly key rotations.
Verifying DKIM signatures is essential to ensure they are working correctly. Several tools and techniques are available for this purpose.
You can check DKIM authentication results in the email header. Look for the "Authentication-Results" header, which will indicate whether the DKIM signature is valid. As a word of caution, some ESPs may share DKIM signatures among customers, as noted in a 2015 article on CircleID.com. If your ESP shares DKIM signatures, it doesn't necessarily affect the uniqueness of the signature itself for your specific emails, but it means you might not have full control over the key management. You'd need to ensure your ESP's implementation correctly associates the signature with your domain, and you should always verify the signature on your end to confirm it's working as expected.
Keep in mind that implementing DKIM is a crucial step in securing your email communications. Next, we'll explore DMARC and how it builds upon SPF and DKIM.
DMARC: Enforcing Policies and Reporting on Authentication
DMARC acts as the final arbiter in email authentication, determining what happens to messages that fail SPF and DKIM checks. Let's explore how DMARC enforces policies and provides reporting on authentication.
Domain-based Message Authentication, Reporting and Conformance (DMARC) policies tell receiving mail servers how to handle emails that fail authentication checks. DMARC builds upon SPF and DKIM to create a robust framework for email security. This ensures consistent application of authentication results across different email providers.
The three DMARC policy options offer varying degrees of enforcement:
- none: The receiving server takes no specific action. This is useful for monitoring email traffic without impacting delivery.
- quarantine: The receiving server places the email in the spam or junk folder. This provides a moderate level of protection.
- reject: The receiving server blocks the email entirely. This is the strongest level of protection against spoofing.
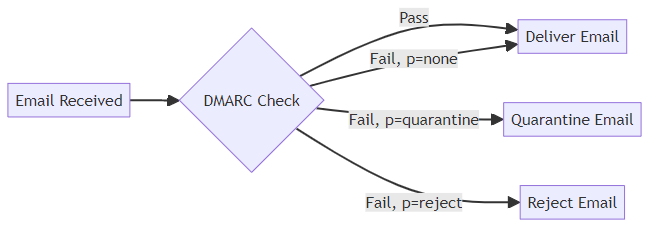
Creating a DMARC record involves defining the desired policy and specifying reporting options. The DMARC record is published as a TXT record in the domain's DNS settings. Proper configuration ensures that receiving mail servers can retrieve and apply the specified policy.
DMARC reporting is crucial for monitoring authentication results and identifying potential issues. Configuring DMARC to send aggregate reports provides valuable insights into email traffic. These reports help domain owners understand how their emails are being authenticated and identify any unauthorized sending sources.
Analyzing DMARC reports allows organizations to identify authentication failures and potential spoofing attempts. DMARC reports provide data on sending sources, authentication results, and actions taken by receiving mail servers. By monitoring these reports, organizations can fine-tune their email authentication practices and improve overall security.
As Email on Acid notes, a key benefit of implementing a DMARC policy is that senders get regular DMARC reports. These reports offer insight into which servers and third parties are sending mail for your domain, the percentage of emails that pass DMARC, and what actions receiving mail servers take on unauthenticated emails.
Implementing DMARC effectively enhances email security and protects against spoofing. Next, we will explore Brand Indicators for Message Identification (BIMI).
BIMI: Displaying Brand Logos in the Inbox
Want to make your brand stand out in a crowded inbox? Brand Indicators for Message Identification (BIMI) offers a way to display your verified logo next to your emails.
BIMI is an email specification that enables senders to display a verified, trademarked logo next to their messages in the inbox. Unlike SPF, DKIM, and DMARC, BIMI provides a visual indicator of trust, making your emails instantly recognizable. BIMI relies on having a fully functional DMARC policy in place with SPF and DKIM records set up, as noted by Email on Acid.
Here's how BIMI works:
- You need a properly formatted logo in SVG format.
- The logo must be a registered trademark.
- A BIMI record is added as a TXT record to your domain's DNS.
Implementing BIMI involves several steps to ensure your logo is displayed correctly.
- Ensure DMARC Compliance: BIMI requires a DMARC policy with SPF and DKIM in place.
- Create a Trademarked Logo: Your logo must be a registered trademark.
- Format the Logo: The logo must be an SVG file in the shape of a perfect square with a solid background and should not exceed 32kb.
- Publish the BIMI Record: Add the BIMI record to your domain's DNS settings.
BIMI offers several key advantages for email senders:
- Increased Brand Visibility: BIMI helps your brand stand out in the inbox.
- Enhanced Trust and Credibility: The verified logo signals that your emails are safe and legitimate.
- Improved Engagement: Visual recognition can lead to higher open rates and engagement.
- Commitment to Security: BIMI demonstrates a commitment to email security best practices.
- Apple Support: Apple Mail supports BIMI logos, with support starting in iOS 16.
Implementing BIMI can help your brand stand out and build trust with your audience. Next, we'll explore testing and troubleshooting email authentication.
Email Testing and Authentication: Ensuring Secure Delivery
Is your email authentication truly effective? Testing is the only way to be sure, and that's where robust email testing tools become indispensable.
Email testing is critical for verifying that your authentication protocols work as intended. It ensures that SPF, DKIM, and DMARC are correctly configured and functioning properly. Without thorough testing, you risk deliverability issues and potential security vulnerabilities.
Here are several types of email tests you can perform:
- SPF Record Validation: Verify that your SPF record includes all authorized sending sources. Incorrect SPF records can lead to legitimate emails being marked as spam.
- DKIM Signature Verification: Ensure that your DKIM signatures are valid and correctly associated with your domain. Invalid signatures can damage your sender reputation.
- DMARC Policy Enforcement: Test how receiving mail servers handle emails that fail authentication checks based on your DMARC policy. Confirm that the intended actions (none, quarantine, reject) are correctly applied.
Automated email testing offers continuous security by integrating tests into your development pipeline. This helps catch authentication issues early, preventing them from impacting real users.
Disposable email addresses provide a safe way to test email authentication. You can verify your setup without risking real user data or spamming legitimate inboxes. Tools like Mail7 offer disposable email addresses and apis for automated testing.
Mail7 provides a Disposable Email Testing api, fast and reliable email delivery service, enterprise-grade security with encrypted communications, developer-friendly REST api with comprehensive documentation, and allows unlimited test email reception.
Here's a basic example of using Mail7's api to create a disposable email address:
import requests
# api endpoint for creating a disposable email
url = "https://mail7.app/api/email/create"
# Replace with your Mail7 api key
headers = {"Authorization": "Bearer YOUR_API_KEY"}
response = requests.post(url, headers=headers)
if response.status_code == 200:
data = response.json()
email_address = data["email"]
print(f"Disposable email address created: {email_address}")
else:
print(f"Error creating email address: {response.status_code}")
You can use Mail7's api to automate the verification of SPF, DKIM, and DMARC results. This allows you to integrate email security testing into your CI/CD pipelines. Mail7 is a developer-friendly REST api with comprehensive documentation.
To interpret the SPF, DKIM, and DMARC results from the Mail7 api, you'll typically look for specific values indicating success or failure. For example:
- SPF Results:
pass: The sending IP address is authorized by the SPF record.fail: The sending IP address is explicitly denied by the SPF record.softfail: The sending IP address is likely not authorized, but the sender isn't confident enough to issue a hard fail.neutral: The SPF record doesn't provide a definitive pass or fail.none: No SPF record was found for the domain.
- DKIM Results:
pass: The DKIM signature is valid and matches the domain.fail: The DKIM signature is invalid or has been tampered with.none: No DKIM signature was found in the email.
- DMARC Results:
pass: The email passed DMARC alignment (either SPF or DKIM passed and aligned with theFromheader).fail: The email failed DMARC alignment.none: No DMARC record was found or the check couldn't be performed.
The Mail7 api response might return these directly, or in a structured format like:
{
"email": "[email protected]",
"messages": [
{
"id": "msg_123",
"subject": "Test Email",
"from": "[email protected]",
"received_at": "2023-10-27T10:00:00Z",
"authentication_results": {
"spf": "pass",
"dkim": "pass",
"dmarc": "pass"
}
}
]
}
You would then parse this authentication_results object to get the specific spf, dkim, and dmarc values.
Here's an example of how you might fetch and interpret these results:
import requests
# Assuming you have the email_id from the creation step
# For demonstration, let's assume email_id = "some_email_id"
# In a real scenario, you'd fetch this after sending an email to the disposable address
# Placeholder for email_id - you'd get this from a previous step or by listing emails
email_id = "YOUR_EMAIL_ID_HERE"
# api endpoint for fetching email details
url = f"https://mail7.app/api/email/{email_id}"
# Replace with your Mail7 api key
headers = {"Authorization": "Bearer YOUR_API_KEY"}
response = requests.get(url, headers=headers)
if response.status_code == 200:
data = response.json()
# Assuming the authentication results are nested as shown in the JSON example above
if "messages" in data and data["messages"]:
auth_results = data["messages"][0].get("authentication_results", {})
spf_result = auth_results.get("spf", "N/A")
dkim_result = auth_results.get("dkim", "N/A")
dmarc_result = auth_results.get("dmarc", "N/A")
print(f"SPF Result: {spf_result}")
print(f"DKIM Result: {dkim_result}")
print(f"DMARC Result: {dmarc_result}")
# Example interpretation
if spf_result == "pass" and dkim_result == "pass" and dmarc_result == "pass":
print("Email authentication passed all checks!")
elif spf_result == "fail" or dkim_result == "fail" or dmarc_result == "fail":
print("Email authentication failed one or more checks. Investigate further.")
else:
print("Authentication results are inconclusive or not fully available.")
else:
print("No messages found for this email ID or authentication results not present.")
else:
print(f"Error fetching email details: {response.status_code}")
By integrating email testing and authentication into your development workflow, you can ensure secure email delivery. Next, we'll explore troubleshooting common email authentication issues.
Beyond the Basics: Advanced Email Security Considerations
Is your email infrastructure truly secure against modern threats? It takes more than basic authentication to protect sensitive communications. Let's explore advanced measures that developers can implement to bolster email security.
TLS/SSL encryption ensures secure email transmission by encrypting data between email clients and servers. Strong encryption protocols and ciphers are crucial for protecting against eavesdropping and data breaches. Use SMTPS for secure SMTP connections.
StartTLS upgrades unencrypted connections to encrypted ones. Also, implement SMTP MTA-STS policies. MTA-STS (Mail Transfer Agent Strict Transport Security) is a DNS-based policy that tells receiving mail servers to only connect to your mail servers using TLS encryption. It's a way to enforce that all email sent to your domain must be encrypted, complementing other security measures by adding an extra layer of assurance for inbound mail security.
Email security gateways filter and protect against email-borne threats. These gateways mitigate spam, phishing, and malware by analyzing email content and attachments. Cybercriminals exploit every opportunity; gateways provide an essential layer of defense.
Staying current with the latest email security threats and best practices is vital. Continuous monitoring and adaptation are necessary to counter evolving threats. Email security protocols are more than technical solutions; they safeguard sending domains and encrypt messages.
By implementing these advanced measures, developers can create a robust email security posture. This ensures the confidentiality and integrity of email communications.





